-->
Security Update for Microsoft Windows SMB Server (4013389)
SOLUTION: The security patch for Windows 7 is provided in the Microsoft Security Monthly Quality Rollup for. I am trying to find the WannaCry patch for Windows 7 but only XP and 8.1 versions coming up on google. The WannaCry ransomware targets the computers running the outdated Microsoft Windows operating systems like the Windows XP, Windows Server 2003, Windows 7/8. After getting in a computer this malware first tries to connect to a domain name which is hard coded in its source code.
Published: March 14, 2017
Version: 1.0
Executive Summary
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.
This security update is rated Critical for all supported releases of Microsoft Windows. For more information, see the Affected Software and Vulnerability Severity Ratings section.
The security update addresses the vulnerabilities by correcting how SMBv1 handles specially crafted requests.
For more information about the vulnerabilities, see the Vulnerability Information section.
For more information about this update, see Microsoft Knowledge Base Article 4013389.

Affected Software and Vulnerability Severity Ratings
Windows 7 Pro Wanna Cry Patch Download Full
The following software versions or editions are affected. Versions or editions that are not listed are either past their support life cycle or are not affected. To determine the support life cycle for your software version or edition, see Microsoft Support Lifecycle.
The severity ratings indicated for each affected software assume the potential maximum impact of the vulnerability. For information regarding the likelihood, within 30 days of this security bulletin’s release, of the exploitability of the vulnerability in relation to its severity rating and security impact, please see the Exploitability Index in the March bulletin summary.
Note Please see the Security Update Guide for a new approach to consuming the security update information. You can customize your views and create affected software spreadsheets, as well as download data via a restful API. For more information, please see the Security Updates Guide FAQ. As a reminder, the Security Updates Guide will be replacing security bulletins. Please see our blog post, Furthering our commitment to security updates, for more details.
| **Operating System** | [**Windows SMB Remote Code Execution Vulnerability – CVE-2017-0143**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0143) | [**Windows SMB Remote Code Execution Vulnerability – CVE-2017-0144**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0144) | [**Windows SMB Remote Code Execution Vulnerability – CVE-2017-0145**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0145) | [**Windows SMB Remote Code Execution Vulnerability – CVE-2017-0146**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0146) | [**Windows SMB Information Disclosure Vulnerability – CVE-2017-0147**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0147) | [**Windows SMB Remote Code Execution Vulnerability – CVE-2017-0148**](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0148) | **Updates Replaced** |
| **Windows Vista** | |||||||
| [Windows Vista Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| [Windows Vista x64 Edition Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| **Windows Server 2008** | |||||||
| [Windows Server 2008 for 32-bit Systems Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| [Windows Server 2008 for x64-based Systems Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| [Windows Server 2008 for Itanium-based Systems Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| **Windows 7** | |||||||
| [Windows 7 for 32-bit Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012212) (4012212) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows 7 for 32-bit Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012215) (4012215) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3212646](https://support.microsoft.com/kb/3212646) |
| [Windows 7 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012212) (4012212) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows 7 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012215) (4012215) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3212646](https://support.microsoft.com/kb/3212646) |
| **Windows Server 2008 R2** | |||||||
| [Windows Server 2008 R2 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012212) (4012212) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2008 R2 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012215) (4012215) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3212646](https://support.microsoft.com/kb/3212646) |
| [Windows Server 2008 R2 for Itanium-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012212) (4012212) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2008 R2 for Itanium-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012215) (4012215) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3212646](https://support.microsoft.com/kb/3212646) |
| **Windows 8.1** | |||||||
| [Windows 8.1 for 32-bit Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012213) (4012213) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows 8.1 for 32-bit Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012216) (4012216) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205401](https://support.microsoft.com/kb/3205401) |
| [Windows 8.1 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012213) (4012213) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows 8.1 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012216) (4012216) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205401](https://support.microsoft.com/kb/3205401) |
| **Windows Server 2012 and Windows Server 2012 R2** | |||||||
| [Windows Server 2012](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012214) (4012214) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2012](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012217) (4012217) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205409](https://support.microsoft.com/kb/3205409) |
| [Windows Server 2012 R2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012213) (4012213) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2012 R2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012216) (4012216) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205401](https://support.microsoft.com/kb/3205401) |
| **Windows RT 8.1** | |||||||
| Windows RT 8.1[2](4012216) Monthly Rollup | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205401](https://support.microsoft.com/kb/3205401) |
| **Windows 10** | |||||||
| [Windows 10 for 32-bit Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012606)[3](4012606) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3210720](https://support.microsoft.com/en-us/kb/3210720) |
| [Windows 10 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012606)[3](4012606) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3210720](https://support.microsoft.com/en-us/kb/3210720) |
| [Windows 10 Version 1511 for 32-bit Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013198)[3](4013198) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3210721](https://support.microsoft.com/en-us/kb/3210721) |
| [Windows 10 Version 1511 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013198)[3](4013198) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3210721](https://support.microsoft.com/en-us/kb/3210721) |
| [Windows 10 Version 1607 for 32-bit Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013429)[3](4013429) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3213986](https://support.microsoft.com/en-us/kb/3213986) |
| [Windows 10 Version 1607 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013429)[3](4013429) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3213986](https://support.microsoft.com/en-us/kb/3213986) |
| **Windows Server 2016** | |||||||
| [Windows Server 2016 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013429)[3](4013429) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3213986](https://support.microsoft.com/en-us/kb/3213986) |
| **Server Core installation option** | |||||||
| [Windows Server 2008 for 32-bit Systems Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (Server Core installation) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| [Windows Server 2008 for x64-based Systems Service Pack 2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012598) (Server Core installation) (4012598) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | 3177186 in [MS16-114](http://go.microsoft.com/fwlink/?linkid=824826) |
| [Windows Server 2008 R2 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012212) (Server Core installation) (4012212) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2008 R2 for x64-based Systems Service Pack 1](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012215) (Server Core installation) (4012215) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3212646](https://support.microsoft.com/kb/3212646) |
| [Windows Server 2012](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012214) (Server Core installation) (4012214) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2012](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012217) (Server Core installation) (4012217) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205409](https://support.microsoft.com/kb/3205409) |
| [Windows Server 2012 R2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012213) (Server Core installation) (4012213) Security Only[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | None |
| [Windows Server 2012 R2](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4012216) (Server Core installation) (4012216) Monthly Rollup[1] | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3205401](https://support.microsoft.com/kb/3205401) |
| [Windows Server 2016 for x64-based Systems](http://catalog.update.microsoft.com/v7/site/search.aspx?q=kb4013429)[3](Server Core installation) (4013429) | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Critical** Remote Code Execution | **Important** Information Disclosure | **Critical** Remote Code Execution | [3213986](https://support.microsoft.com/en-us/kb/3213986) |
[2]This update is only available via Windows Update.
[3] Windows 10 and Windows Server 2016 updates are cumulative. The monthly security release includes all security fixes for vulnerabilities that affect Windows 10, in addition to non-security updates. The updates are available via the Microsoft Update Catalog. Please note that effective December 13, 2016, Windows 10 and Windows Server 2016 details for the Cumulative Updates will be documented in Release Notes. Please refer to the Release Notes for OS Build numbers, Known Issues, and affected file list information.
*The Updates Replaced column shows only the latest update in any chain of superseded updates. For a comprehensive list of updates replaced, go to the Microsoft Update Catalog, search for the update KB number, and then view update details (updates replaced information is provided on the Package Details tab).
Vulnerability Information
Multiple Windows SMB Remote Code Execution Vulnerabilities
Remote code execution vulnerabilities exist in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerabilities could gain the ability to execute code on the target server.
To exploit the vulnerability, in most situations, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv1 server.
The security update addresses the vulnerabilities by correcting how SMBv1 handles these specially crafted requests.
Included with Xbox Game Pass. Play Forza Horizon 4 and over 100 more great games for one low monthly price with Xbox Game Pass. JOIN XBOX GAME PASS FOR $1 Buy on disc or download. The Forza Horizon 4 Standard Edition digital bundle includes the full game of Forza Horizon 4 and the Formula Drift Car Pack. To download and install Forza Horizon 4 on Windows 10, you need a device running version 1703, with OS Build 15063.0 or later. Additionally, your device must be running a 64-bit version of Windows 10. If you have a 32-bit version, you will not be able to play Forza Horizon 4. Dec 21, 2018 Forza Horizon 4 on XBox One Crashing I just bought an Xbox One S with Forza Horizon 4 last week and have had it continually crash and shut the game down while playing. Is this an issue with the game the system or both. Forza Horizon 4 day one update for Xbox One and Windows 10 is now available for download. According to the official Forza Horizon 4 day one update patch notes, the new patch has added fixes for stuttering/lag, game crashing, and UI bugs. Forza horizon 4 xbox one cheats.
The following table contains links to the standard entry for each vulnerability in the Common Vulnerabilities and Exposures list:
| **Vulnerability title** | **CVE number** | **Publicly disclosed** | **Exploited** |
| Windows SMB Remote Code Execution Vulnerability | [CVE-2017-0143](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0143) | No | No |
| Windows SMB Remote Code Execution Vulnerability | [CVE-2017-0144](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0144) | No | No |
| Windows SMB Remote Code Execution Vulnerability | [CVE-2017-0145](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0145) | No | No |
| Windows SMB Remote Code Execution Vulnerability | [CVE-2017-0146](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0146) | No | No |
| Windows SMB Remote Code Execution Vulnerability | [CVE-2017-0148](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0148) | No | No |
| **Vulnerability title** | **CVE number** | **Publicly disclosed** | **Exploited** |
| Windows SMB Information Disclosure Vulnerability | [CVE-2017-0147](http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0147) | No | No |
For Security Update Deployment information, see the Microsoft Knowledge Base article referenced here in the Executive Summary.
Csgo winter update 2015 patch download. [WINTER SEASON FUN] – Chickens are now sporting their festive-wear to celebrate the season. – Players can now pick up and throw snowballs in all game modes except Danger Zone, Wingman, and Competitive Matchmaking. Cologne 2014 Operation Breakout Update EMS One CS:GO Championship. Including myself. I want the old csgo back! Dec 8, 2015 @ 9:44pm. Small but it runs everything wonderfully. Used to run CS:GO with no problems at all, perfect quality. Now, after the winter update, I can't even seem to move around without massive frame drop and lag. They released a patch. Hopefully it will fix it #13. Release Notes for 12/8/2015. 2015.12.08 - [WINTER UPDATE] – Slight adjustments to Holiday Cheer. These are also the new times for CSGO Major Championships. Katowice 2014 Operation Phoenix Update Stickers Workshop Update Introducing the cz75-auto The winter offensive holiday update Introducing Cobblestone and Overpass. CS:GO update – the latest changes to the world’s best FPS What are the latest buffs, nerfs, and changes to Counter-Strike? Here are the patch notes for the most recent CSGO update. The Winter Offensive Update is shipping with three types of gifts for the giving. The Winter Offensive Case. Presenting the first-ever community-made case, featuring some of the most popular and interesting finishes from the CS:GO Workshop on a wide variety of weapons. The Esports Winter Case.
Acknowledgments
Microsoft recognizes the efforts of those in the security community who help us protect customers through coordinated vulnerability disclosure. See Acknowledgments for more information.
Disclaimer
The information provided in the Microsoft Knowledge Base is provided 'as is' without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including the warranties of merchantability and fitness for a particular purpose. In no event shall Microsoft Corporation or its suppliers be liable for any damages whatsoever including direct, indirect, incidental, consequential, loss of business profits or special damages, even if Microsoft Corporation or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for consequential or incidental damages so the foregoing limitation may not apply.
Revisions
Wannacry Patch Download
- V1.0 (March 14, 2017): Bulletin published.
Page generated 2017-05-08 07:15-07:00. Digimon 3ds patch download download.
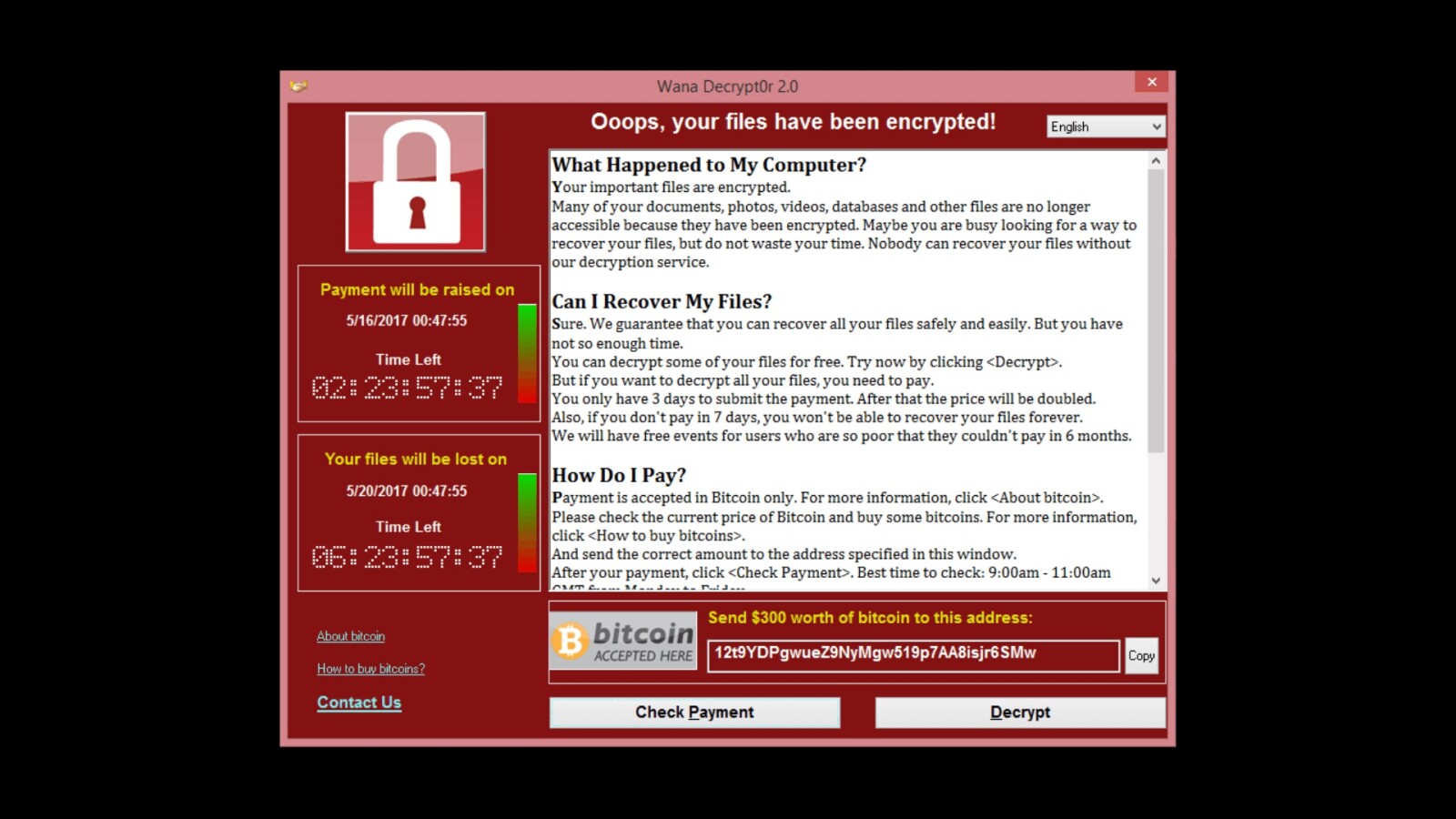
A global ransomware campaign, called WannaCry, has now infected over 10,000 organizations and 200,000 individuals in over 150 countries, including the UK National Health System which saw ambulances divert from affected hospitals. After a killer switch was activated by a security research simply registering a domain that stopped the original ransomware, new variants of the WannaCry started emerging.
The ransomware was developed to exploit the vulnerability in SMB used in a Windows-based network environment. Because of that, Linux, Mac OS are not affected by this widely spread ransomware. Windows 10 Creators Update computers are also not affected by WannaCry since the operating system already has this vulnerability patched up out of the box.
So, how to protect yourself from WannaCry Ransomware
1. Install the patch that Microsoft has released back in March to block the specific exploit that WannaCry is using. See more details below.
Lol past patch download. 2. Update your anti-virus software definition. Most AV vendors have now added detection capability to block WannaCry.
3. If you don’t have any anti-virus software installed, you should consider install or enable Windows Defender (Security Essentials) which is free.
4. Backup, backup and backup. One of the fundamental defense against ransomware is the ability to reliably restore from backup.
What patch do I need for my machine?
The patch was released in March, namely Microsoft Security Bulletin MS17-010, which addresses the vulnerability that these attacks are exploiting. Basically, you can get your computer patched up through either Windows Update or install manually through Microsoft Update Catalog. Microsoft also made an exception and released security patches for their legacy operating systems such as Windows XP, Vista, and Windows Server 2003. You can find all individual patches and download them from Microsoft Update Catalog website.
If you have Windows Update set up to install updates automatically, your computer is most likely already patched up. But how do I now if that’s the case?

You can go to “View update history” in Windows Update in Control Panel to find out. Here are the list of KB numbers for this patch on various Windows systems.
- Windows Vista & Windows Server 2008: KB4012598
- Windows 7 & Windows Server 2008 R2: KB4012212 (Security Only) or KB4012215 (Monthly Rollup)
- Windows 8.1: KB4012213 (Security Only) or KB4012216 (Monthly Rollup)
- Windows Server 2012: KB4012214 (Security Only) or KB4012217 (Monthly Rollup)
- Windows Server 2012 R2: KB4012213 (Security Only) or KB4012216 (Monthly Rollup)
- Windows 10
- First release: KB4012606
- Version 1511: KB4013198
- Version 1607: KB4013429
- Windows 2016: KB4013429
What if I can’t patch my computer at the moment?
Well, you should consider disabling the vulnerable SMBv1 on all unpatched computers.
To disable SMBv1 on Windows 7, Windows Server 2008, Windows Server 2008 R2, Windows 8, and Windows Server 2012
To remove SMBv1 in Windows 2012 R2, and Windows Server 2016
Open Server Manager and launch Remove Roles and Features Wizard to remove SMB 1.0/CIFS File Sharing Support feature.
To remove SMBv1 from Windows 8.1 and Windows 10 computers
Open Control Panel and Turn Windows features on or off, and turn off SMB 1.0/CIFS File Sharing Support from the list.
Lastly, for further reading, Microsoft has released customer guidance for the WannaCry attacks and Troy Hunt has done an excellent detailed write-up on the WannaCry ransomware.
Related Posts
Windows Xp Wanna Cry Patch Download
Hmm…maybe try the one listed in the following link: